Secure Network Access Solutions
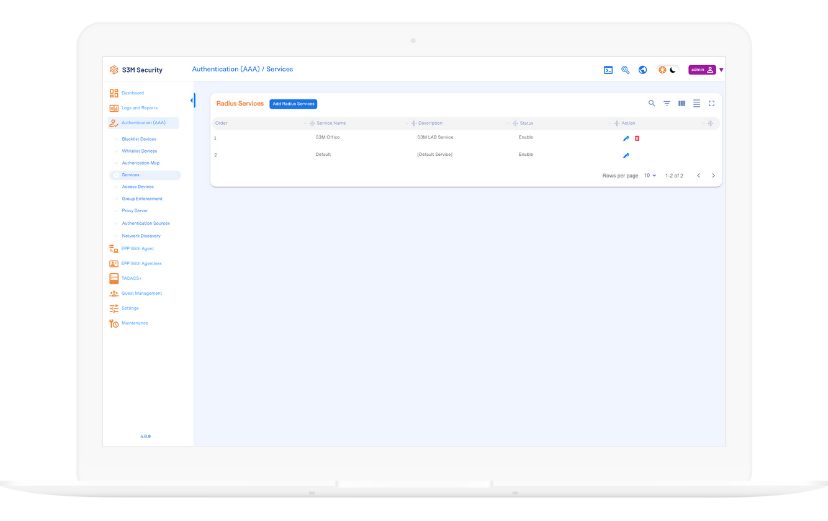
S3M Security protects your network by verifying user identities before granting access to network resources. Using 802.1X or MAC Authentication methods, it ensures that only authorized individuals can connect.
During authentication, credentials are validated against systems such as Active Directory, LDAP, Oracle, SQL, or local databases, ensuring secure and appropriate access.
Vendor-Agnostic Architecture for Maximum Flexibility
S3M Security features a vendor-agnostic design that works seamlessly with devices from different manufacturers. It operates in compliance with industry standards set by organizations like IETF and IEEE, ensuring compatibility across a wide range of network infrastructures.
S3M ConnGuard NAC
How You Can Use S3M Security ConnGuard NAC
Identity Verification Across Wired, Wireless, APN, and VPN Networks:
Ensure users are properly authenticated across all types of network environments.
Network Access Control and Reporting Management:
Manage who can access your network and generate detailed reports for full visibility.
Automated Health Checks with UEM Integration:
Seamlessly perform device health assessments through Unified Endpoint Management (UEM) systems to ensure compliance.
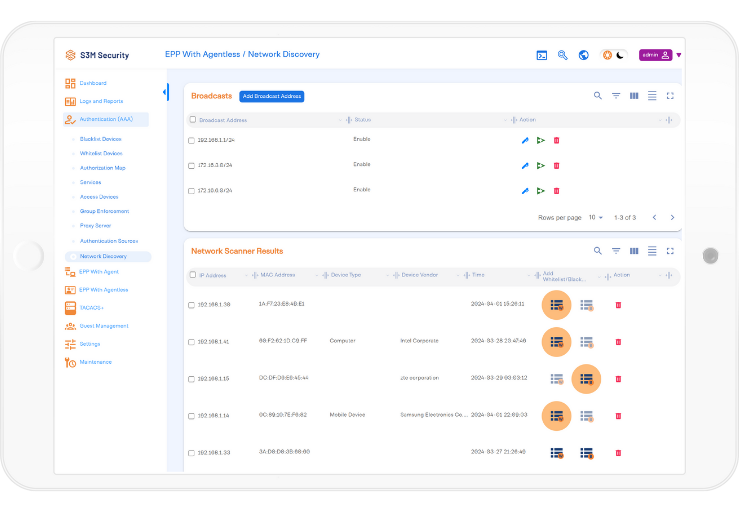
Network Discovery and Device Blacklisting:
Automatically scan all subnets to detect unauthorized devices and blacklist them instantly.
The Tri-Fold Security Strategy
The AAA module delivers a comprehensive security solution through
Rigorous verification of user identities serves as the first checkpoint, thwarting access attempts by unauthorized users.
After authentication, this step ensures users can only access resources appropriate to their authorization level, mitigating the risk of internal data breaches.
Detailed tracking of user activity within the network creates an audit trail, enhancing visibility and accountability, which is crucial for identifying and responding to security incidents.